To trace the account lockout source machine in Active Directory, there are several methods available. One way is to enable account lockout events in the domain controller logs by enabling the audit policies for your DCs. Another way is to use PowerShell scripts to identify the source of the locked-out user. You can also try using tools like LockoutStatus or Netwrix Account Lockout Examiner to diagnose the issue. Additionally, you can track the locked-out accounts and find the source of AD account lockouts by following a few steps.
It is important to identify the source of the account lockout to prevent future lockouts and ensure the security of your Active Directory environment.
If you dont have access to any of the tools mentioned above, you are still not out of luck. Just follow along.
Pre-Requisite
To enable account lockout events in domain controller logs, you need to enable the following audit policies for your DCs. Go to the GPO section Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Advanced Audit Policy -> Logon/Logoff and enable the following policies: Audit Account Lockout, Audit Logon, and Audit Logoff
Once these policies are enabled, you can find the domain account lockout events in the Security log on the domain controller (Event Viewer -> Windows Logs). Filter the security log by the EventID 4740 to see a list of the latest account lockout events
How do you find the domain controller to check the Security logs?
Ideally, you should check this on your DC that hosts the PDC Emulator role. To find your logon DC, run the below from a command prompt
set l
You will get a result as below

The logon server is the domain controller that processed your login request. Take note of that and RDP to that machine to check the event logs or you could do a remote connection to the Event Viewer on the DC from whichever server you are currently on.
Navigate to the Security logs and right click and select “Filter Current Log“
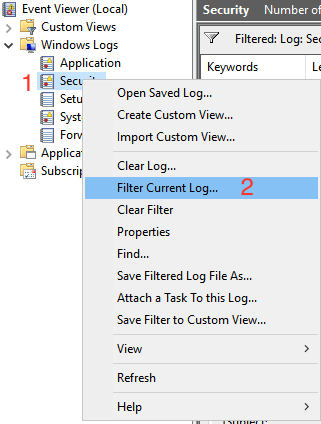
Select a time period, and specify the event ID as 4740 and click Ok

In the filtered logs, find the log that mentions the account that you are after. Here in my case, i am trying to find the root cause of my own account lockout ;).

The most important piece of info in these event logs is the “Caller Computer Name” which is the server (the one marked with an arrow) that is locking out your account in the Active Directory domain.

Once you have that info, you can check if there are any connections on that VM by running the below
quser /server:<servername>

You can then logoff the account remotely by running the below
logoff /server:<servername> <sessionID>
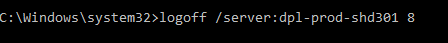
You may have multiple logons on different servers so ensure that you capture all the servers that are complaining about your previous logins under an old password which is one of the most common reasons for account lockouts.
What if I want to find the account lockout root cause for more than one user?
LockoutStatus is a fantastic tool that displays lockout information about a particular user account. It is a combination command-line and graphical tool that collects information from every contactable domain controller in the target user account’s domain.
The tool makes it easy to find all locked users, unlock accounts, reset passwords, and troubleshoot locked-out users. To use LockoutStatus, you need to download it from here and install the tool on your computer that’s joined to the same domain where you want to query for account lockouts. Once installed, you can run the tool and enter the user account name to check the lockout status and find the source of the lockout. That’s all there to it.
I will wrap up this post with that. Hopefully someone is going to find this useful. Have a good one peeps!

Leave a comment