Category: Remote Desktop Services
-
Configure RDP Proxy in NetScaler
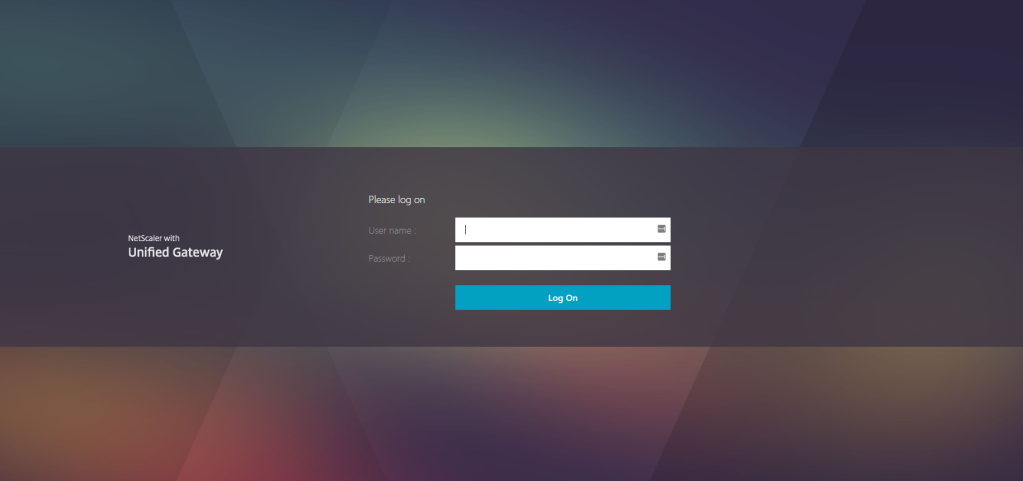
The RDP Proxy functionality is provided as part of the Citrix Gateway and currently is available to all NetScaler Enterprise and Platinum customers. The following RDP Proxy features provide access to a remote desktop farm or an RDSH session host server through Citrix Gateway: Secure RDP traffic through CVPN or ICAProxy mode (without Full Tunnel).…
-
script to restart print spooler service
The below VB script can be used to restart print spooler service at regular intervals with Windows task scheduler. ‘====================================== ‘This script serves as a workaround to poorly written printer drivers ‘ ‘It checks the spooler folder to see if there are any active jobs. ‘If it is empty it will restart the spooler service.…
-
How to troubleshoot “The Terminal Server security layer detected an error in the protocol stream and has disconnected the client. Client IP:” and “The RDP protocol component X.224 detected an error in the protocol stream and has disconnected the client”error messages
Problem Description : You may experience problems if you try to connect to a Windows Server 2008 R2 via RDP. This can also occur in a XenDesktop 7 site with a Windows Server 2008 R2 broker server. Symptoms : – RDP Session may freeze. – Black screen inside RDP window. – Slow connection. – You…
